Content
- Part 1: Zero-Knowledge Proofs
- What are Zero-Knowledge Proofs
- Origins of Zero-Knowledge Proofs
- Understanding Zero-Knowledge Proofs Through Examples
- The Dominant Types of ZKPs
- zk-SNARKs
- zk-STARKs
- Comparison
- Conclusion
- Part 2: Current and Future Applications of Zero-Knowledge Proofs
- Applications of Zero-Knowledge Proofs
- Scaling Blockchains
- Voting
- Privacy Tokens and Private Transactions
- Privacy-Preserving Data Storage
- Future Applications of Zero-Knowledge Proofs
- Digital Verifiable Identities
- Combating MEV Through Zero-Knowledge Ethereum Mempool
- ZK Auctions
- Conclusion
- About Zerocap
- DISCLAIMER
- FAQs
- What are Zero-Knowledge Proofs (ZKPs) and how do they work?
- What are the origins of Zero-Knowledge Proofs?
- What are the dominant types of Zero-Knowledge Proofs?
- What are the current and potential future applications of Zero-Knowledge Proofs?
- How do Zero-Knowledge Proofs contribute to privacy and security in blockchain technology?
2 May, 23
Zero-Knowledge Technology: Functions and the Future

- Part 1: Zero-Knowledge Proofs
- What are Zero-Knowledge Proofs
- Origins of Zero-Knowledge Proofs
- Understanding Zero-Knowledge Proofs Through Examples
- The Dominant Types of ZKPs
- zk-SNARKs
- zk-STARKs
- Comparison
- Conclusion
- Part 2: Current and Future Applications of Zero-Knowledge Proofs
- Applications of Zero-Knowledge Proofs
- Scaling Blockchains
- Voting
- Privacy Tokens and Private Transactions
- Privacy-Preserving Data Storage
- Future Applications of Zero-Knowledge Proofs
- Digital Verifiable Identities
- Combating MEV Through Zero-Knowledge Ethereum Mempool
- ZK Auctions
- Conclusion
- About Zerocap
- DISCLAIMER
- FAQs
- What are Zero-Knowledge Proofs (ZKPs) and how do they work?
- What are the origins of Zero-Knowledge Proofs?
- What are the dominant types of Zero-Knowledge Proofs?
- What are the current and potential future applications of Zero-Knowledge Proofs?
- How do Zero-Knowledge Proofs contribute to privacy and security in blockchain technology?
Part 1: Zero-Knowledge Proofs
The cryptocurrency space is built on the shoulders of cryptography; innovations in this field eventuate in blockchain technologies advancing, becoming more scalable and safe. One cryptographic breakthrough that has meaningfully benefited blockchains and protocols is Zero-Knowledge proofs (ZKPs). These mathematical approaches to proving statements can be used to securely and verifiably compress sizable quantities of data, giving it many applications in the blockchain space.
This part of the research piece will examine what zero-knowledge (ZK) is, its origins, how it works and the different cryptographic models emerging from within this category.

What are Zero-Knowledge Proofs
ZKPs are a mathematical concept that enables one party to prove that a statement is true to another party without revealing any information about the statement. As such, these proofs enable individuals to establish truth without elucidating how that truth was reached or the contents of what underpins the truth. A prover can establish to a group of verifiers that they know some secret without giving that secret away. In the context of trustless blockchains, ZKPs have clear use cases in conveying data without the fear that the veracity of the data will be questioned or undermined.
The existence of this cryptographic primitive is groundbreaking; one can prove they know or do not know, something whilst simultaneously conveying zero-knowledge about that something. The ambiguity of that statement can be overcome through a real-world example; Yao’s Millionaire Problem. Imagine that there are two millionaires that each wants to know which is the richest without disclosing their wealth. Any solution to this problem is a ZKP. Clearly, these types of proofs can revolutionise privacy; passwords will no longer be necessary to login into accounts, only a ZKP that an individual knows their password. Digital signatures and identifications can be efficiently checked without the owner needing to give away any confidential information about themselves.
Through time, three key criteria were ascertained which had to be satisfied in order for a proof statement to be ZK. Proofs must be complete; if an input is valid, meaning the underlying statement is true, a ZK protocol will consistently display this. Furthermore, Zero-Knowledge protocols must be sound; no invalid input can result in the proof returning true – an honest verifier will always perceive this to be false. Finally, protocols are only classified under the ZK hypernym if the verifier learns nothing about the conveyed statement beyond its truth or falsity. If the input can be extracted from the protocol, then it is not ZK.
Origins of Zero-Knowledge Proofs
Although the effectiveness of ZKPs has heralded an exponential increase in unique use cases, cryptography has been developed and improved over more than 30 years. The concept of ZKPs was first denoted in Shafi Goldwasser, Silvio Micali and Charles Rackoff’s 1985 paper, entitled “The Knowledge Complexity of Interactive Proof-Systems”. Their paper introduced a language called Zero-Knowledge Interactive Proof Systems (ZKIP). This language provided a latticework to engage in simple interactive proofs in nondeterministic polynomial time. ZKIP outlined a means to prove certain statements as true without revealing information about those statements or the data used to construct them.
Three years after the initial paper establishing interactive ZKPs, Manuel Blum, Paul Feldman and Silvio Micali unveiled their research on these proofs, depicting that interactions in ZKPs can be replaced by both parties having access to a random string. Their paper, titled “Non-Interactive Zero-Knowledge and Its Applications”, leveraged encryption techniques, including Shamir’s Secret Sharing Scheme (SSS), to increase the ease of adopting these proving systems once both parties had access to the same string.
Understanding Zero-Knowledge Proofs Through Examples
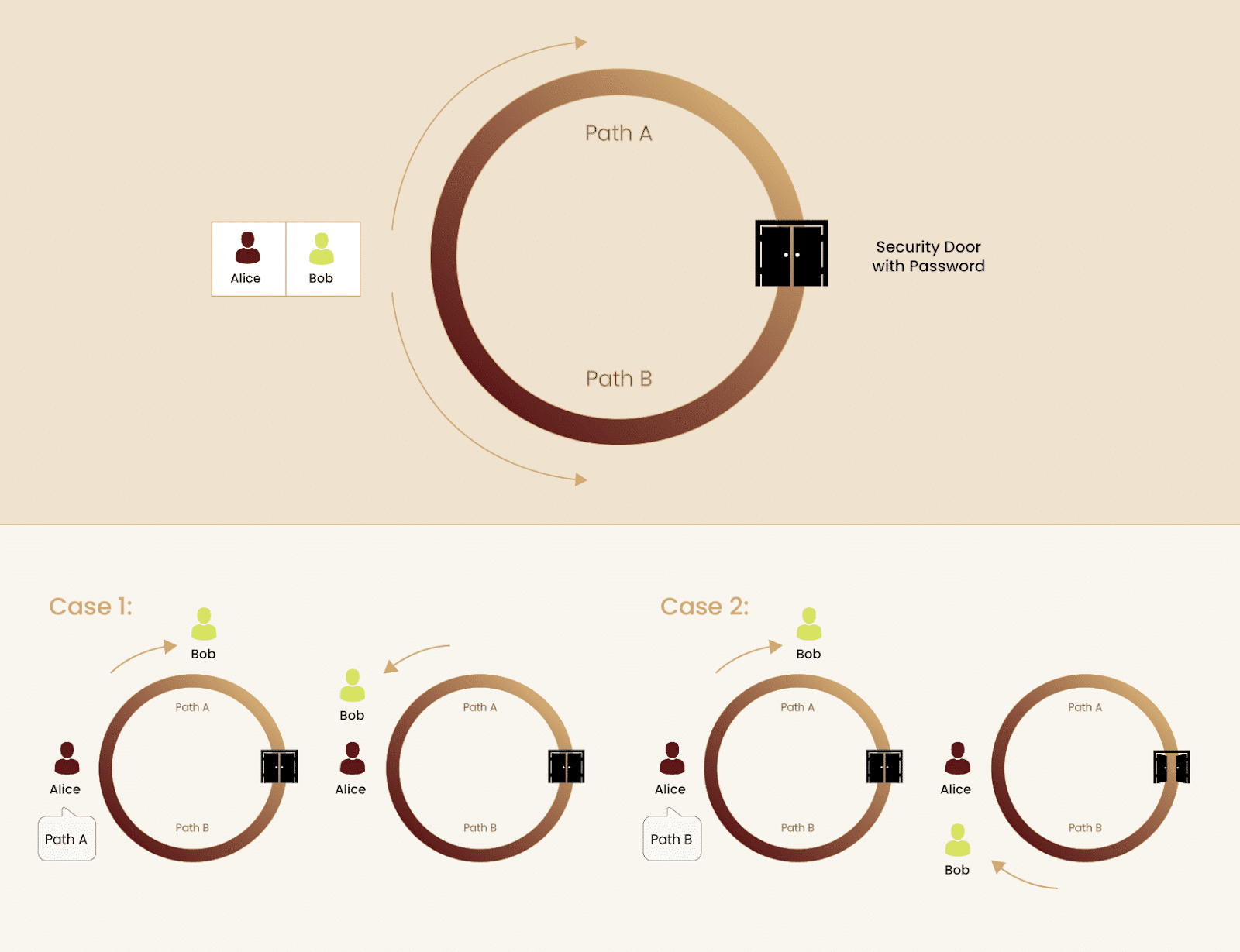
Establishing a truth without revealing external information is a foreign concept; irrespective of whether the history of the cryptographic primitive is known. Hence, ZKPs are commonly conveyed through the Ali Baba Cave analogy. In this example, there is a circular cave with a door in the middle of the cave, directly opposite to the entrance. For an individual walking into the cave, they would see a divergence in the path – the left side is labelled “Path A” and the right side “Path B”. Upon opening, the central door leads the alternate path, however, it requires a password to unlock. For example, if Bob entered from Path B and knew the password, he would exit from Path A.
As with all ZKPs, the prover must establish truth without giving any other information to the verifier; here, Bob must prove he knows the password to the cave’s door without telling it to Alice. Bob, the prover, enters the cave whilst Alice, the verifier, turns around, unaware of which path Bob followed. Subsequently, Alice calls out the path she wants Bob to exit from. Obviously, Bob could get lucky once or twice wherein he enters the path that Alice calls out, not requiring him to use the password. Yet, there is a 50% chance that, in the long run, Alice requests Bob to exit from the path he did not enter. In order for Bob to successfully prove his knowledge of the passcode, he must invariably emerge from Alice’s requested path. Of course, if Bob has the correct password for the door, he will never fail the task, thereby satisfying the ZKP. Through this proof, Bob displayed to Alice that he knows the password yet did not share any details of it.
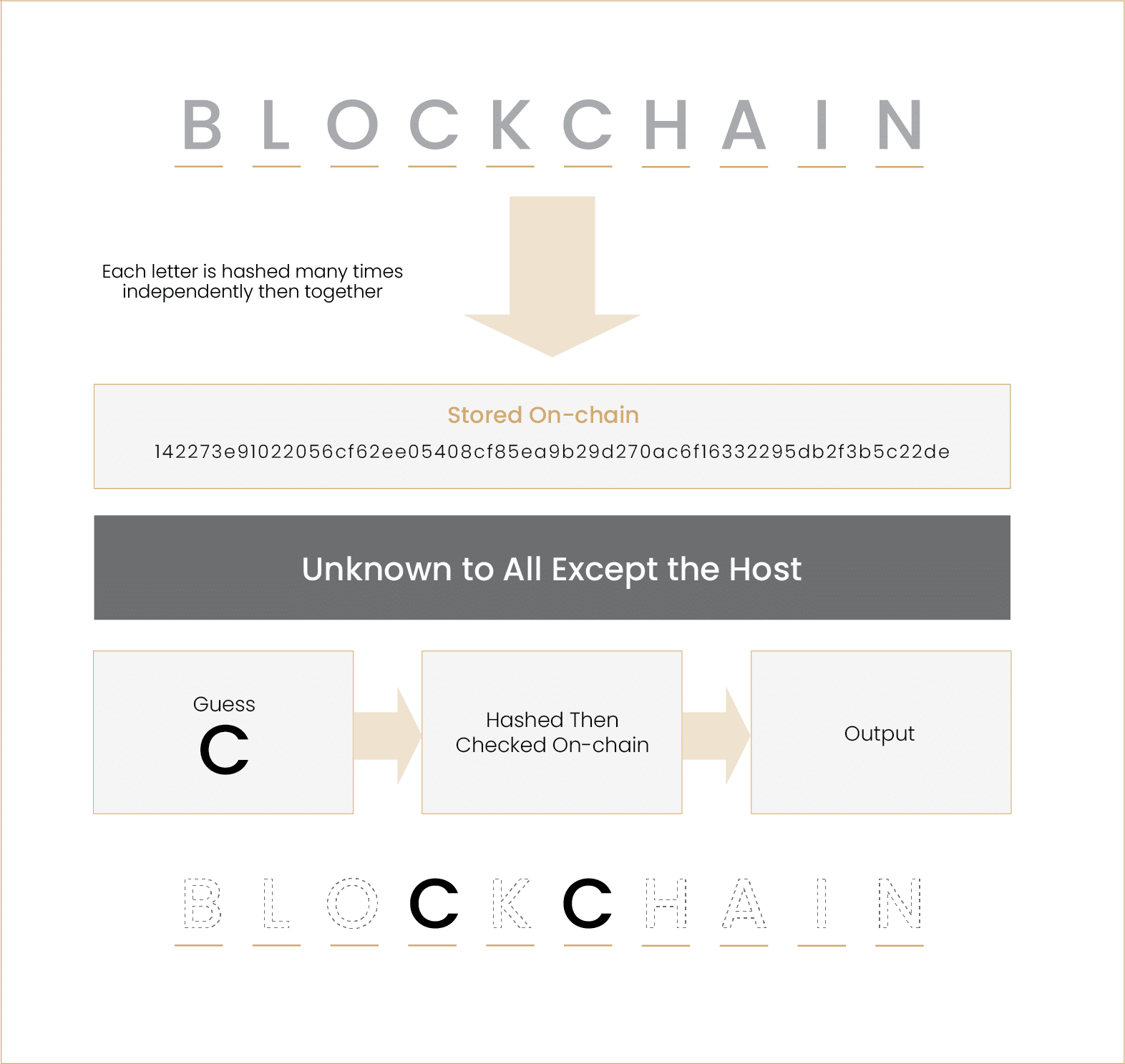
Another framework to understand the intricacies of ZKPs, including the need for them, is through a Zero-Knowledge version of Hangman. When the host chooses their word, no one but them knows it. However, if the game is being played online, the host must select their word and submit it; the word is then stored on the game’s server. Introducing a third party into this dynamic results in the hangman players trusting this party, the server, to store the determined word. However, certain players with the correct expertise will be able to ascertain the word from the server.
ZKPs can be integrated into the game so as to ensure the players’ trust that any letter they guessed is part of the host’s word, without anyone but the host knowing the word. Rather than the host storing the word on a centralised server, a cryptographic approach similar to Merkle Trees can be leveraged wherein each letter is hashed individually and subsequently together until a hashed root letter is obtained. This method enables players to guess letters and see if their input, after being modified like the host’s word, lines up with the root letter. If it does, their guess was correct; this truth can be displayed via a step-by-step ZKP without conveying any other letters of the word.
The Dominant Types of ZKPs
There are evidently a significant number of use cases for Zero-Knowledge, sparking the need for a plethora of various ZKPs to achieve different purposes. To satisfy these unique situations, zk-SNARKs and zk-STARKs emerged to prove that certain computation is correct.
zk-SNARKs
The original ZKP, arising out of the Shafi Goldwasser, Silvio Micali and Charles Rackoff’s design, is a zk-SNARK. Standing for Zero-Knowledge Succinct Non-Interactive Argument of Knowledge, zk-SNARKs strive to generate proofs to accentuate knowledge using secret keys without interacting with the verifier. These succinct ZKPs can be verified within milliseconds irrespective of the proof length for larger statements. Many blockchains utilise these ZKPs to determine whether blocks of transactions satisfy consensus rules without exposing the underlying information to other network participants. Information is transformed into equations that can be proved via cryptographic keys.
However, herein lies a fault of zk-SNARKs, all parties involved with the proof must know the secret key. This means that a trusted setup, wherein provers and verifiers trust each other and a single proof generator, is required, allowing relevant entities to obtain the private key. Nonetheless, with zk-SNARKs utilised throughout the crypto ecosystem, many companies are working on generating such proofs without the need for a trusted ceremony.
zk-STARKs
Forking the path of the evolution of zk-SNARKs, StarkWare, a company focused on scaling Ethereum through ZKPs and rollups, created a new variation of proofs – Zero-Knowledge Scalable Transparent Argument of Knowledge (zk-STARKs). Unveiled in StarkWare’s 2018 paper entitled “Scalable, transparent and post-quantum secure computational integrity”, this proof system revolutionised ZKPs by eliminating the need for a reliable, trusted setup of the cryptographic keys. This was achieved by relying primarily on hash functions.
Moreover, although zk-SNARKs are succinct, zk-STARKs innovated by taking computation and storage off-chain to a STARK prover; this reduces transaction and verification costs exponentially. Notably, the verification of all zk-STARK proofs can be verified as all ZKPs are posted on-chain. In this sense, zk-STARKs can promote scalability without sacrificing transparency.
Comparison
Both zk-SNARKs and zk-STARKs can be used to create ZKPs, including the technology for verifiers and provers. Given that zk-STARKs have primarily gained traction within the context of scaling Ethereum, they have fewer applications when it comes to generating ZKPs that do not relate to compressing on-chain transactions. Similarly, when examining the proof size of these variations of ZKPs, zk-SNARKs have an average size of 288 bytes, far outperforming that of zk-STARK proofs which can range from 45KB-200KB. As such, zk-SNARKs are estimated to use only 24% of the gas required by zk-STARKs.
Fundamental to zk-STARKs is the absence of a trusted ceremony, offering a substantial benefit in regards to decentralisation over the alternative form of ZKPs. Moreover, as the STARK prover generates proofs off-chain, zk-STARKs are meaningfully more scalable that zk-SNARKs. Furthermore, through leveraging specific hash functions, Merkle Trees and a unique random oracle model, zk-STARKs offer quantum security. Traditional encryption models that are founded upon the RSA algorithm to generate public and private keys, integral to zk-SNARKs, are highly vulnerable to quantum computing attacks.
Although the developer community is supporting both ZKP systems, due to the larger proof sizes of zk-STARKs when compared to zk-SNARKs, utilising the former is substantially more arduous. Moreover, in order to leverage the benefits offered by StarkWare’s ZKPs, developers must learn and code in the company’s programming language, Cairo. Notwithstanding, other community leaders have displayed their support for the creation and continued development of zk-STARKs. The Ethereum Foundation has championed the emerging technology by providing StarkWare with a US$ 12 million grant.
Conclusion
ZKPs are gradually becoming more relevant to the multifaceted industry of cryptocurrency. Although there are already numerous types of proofs and various use cases, it is not challenging to envision a future where payments, seeking loans and logging into platforms utilise ZKPs. By mitigating trust and simultaneously escalating privacy, ZKPs have the potential to give individuals power over their knowledge and information.
This part of the research piece focused on what and how these proofs work; the next part will elucidate the current state of ZK in the crypto space, including its use cases as well as areas that can see major benefits from the technology.
Part 2: Current and Future Applications of Zero-Knowledge Proofs
Leveraging novel technologies to improve existing models is fundamentally crucial to advancing the blockchain industry. ZKPs are rapidly becoming an important factor in developers’ crypto toolkits given their ability to impressively compress data, provide privacy across all blockchain sectors and more. This part of the article will examine existing and possibly forthcoming applications for ZK technology with respect to their benefits, limitations and wider market impacts.
Applications of Zero-Knowledge Proofs
Scaling Blockchains
Currently, the primary application for ZKPs is scaling Ethereum and assisting “The World Computer” in achieving its rollup-centric roadmap. Ethereum’s mainnet is known as a layer 1 blockchain; it facilitates the execution of smart contracts, settles transactions, stores on-chain data and allows nodes to reach consensus. However, given that a single, monolithic chain is performing all these crucial tasks, it fails to scale. Until now, Ethereum’s concentration has been on championing security and decentralisation over scalability. Nonetheless, rollups herald in a method to modularise the roles of blockchains, enabling chains like Ethereum to scale as thousands of transactions are being executed by a network built on top of the layer 1; hence, these networks are known as layer 2s.
These networks bundle up a significant number of transactions, compress them through rolling up all the transactions into a single proof and posting this on the mainnet. This enables layer 2s to provide an efficient forum for transactors whilst concurrently leveraging Ethereum’s lauded levels of security and decentralisation. ZKPs have the capacity to effectively respond to the blockchain trilemma through bringing scalability to layer 1 blockchains focused on the other two prongs. Networks like StarkNet by StarkWare and zkSync by Matter Labs compress transactions through the use of ZK technology. This allows for meaningful scalability as verifiers of these transactions can review the proof and comprehend its veracity without actually being cognisant of the specific transactions themselves. Accordingly, the need to unsustainably store vast amounts of data is mitigated.
Despite the use of cryptographic, zero-knowledge primitives to scale these blockchains, it is important to specify the difference between the use of ZKPs and validiums. Although modular blockchains like Celestia and Fuel Labs are looking to add a dedicated data availability layer to the blockchain stack, currently, the cost of computing and executing proofs is exorbitant. As such, validiums emerged with a solution to execute transactions off-chain and submit a validity proof. Unlike a zero-knowledge rollup (ZKR) which would store the data directly on Ethereum, validiums store data off-chain and verify it with a randomly selected committee. Despite their minor difference, ultimately, both ZKRs and validium-based rollups achieve the same purpose of scaling blockchains with the use of ZK technology
Voting
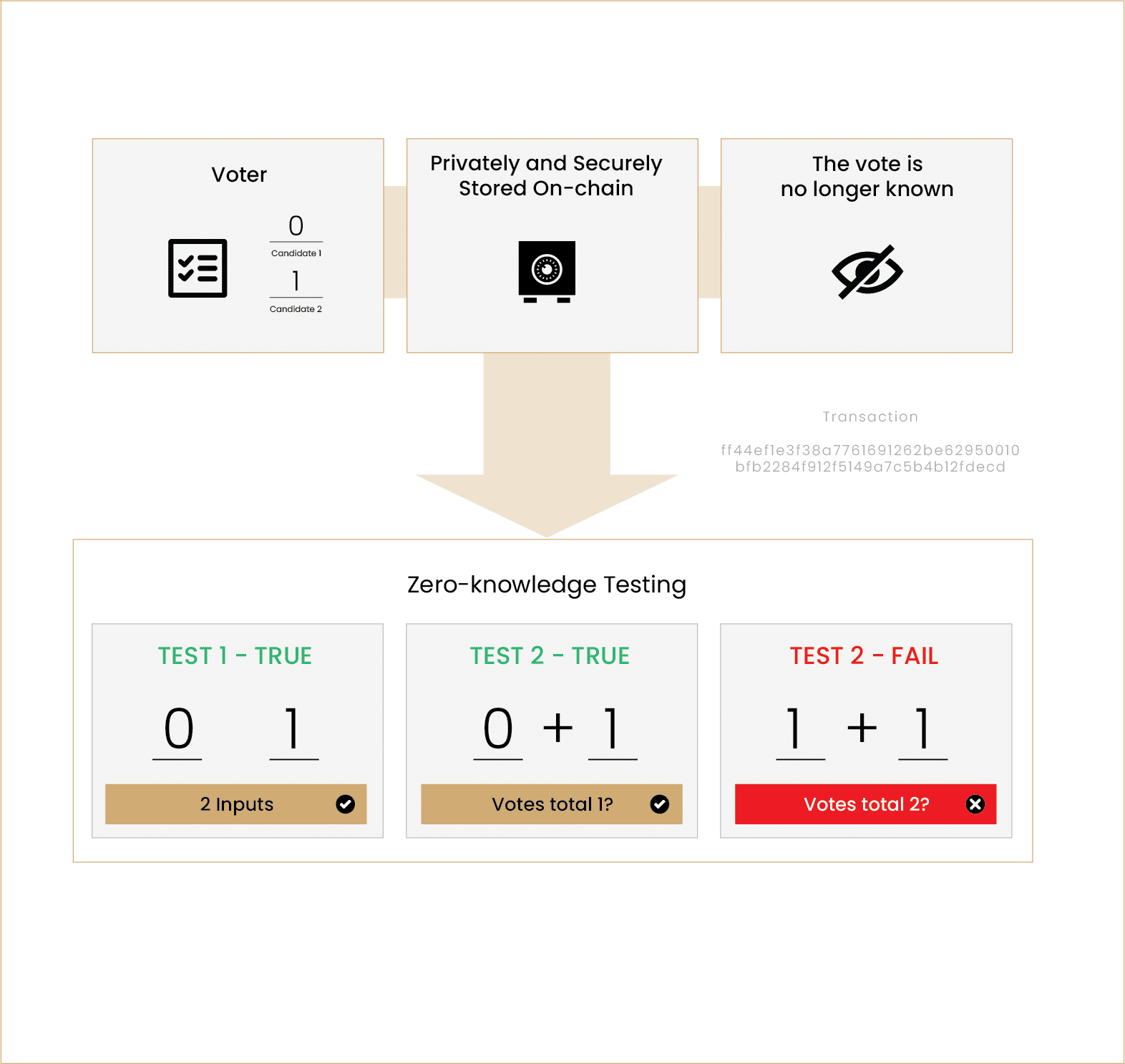
As well as using ZKPs to power rollups and scale congested blockchains, within the web3 world, ZK can be used to protect restricted and privileged information. Voting is an example of an industry which would benefit from the use of ZKPs. Whether it be for voting in Decentralised Autonomous Organisations (DAOs) or parliamentary elections, if individuals can cast their votes with the certainty of privacy, genuine participation might increase. In this context, no votes would be stored by any authority, but rather posted on a permissioned/permissionless blockchain through a ZK circuit. This circuit will ostensibly randomise the vote, however, the augmentation to the input will be deterministic, meaning that it can be used to count votes.
However, if votes are not seen or counted by an individual or machine, how can DAOs and other organisations be sure that votes are valid? This too can be achieved through a series of Zero-Knowledge tests. If an entity could vote on 2 options with a 1 or a 0, indicating they voted for the first option, the first verification test might be to determine whether or not their inputs were either 1 or 0. Subsequently, to ensure the entity only voted for 1 option, the verifier can add up the inputs. If they sum to 1 and there are two votes, one must be a 1 and the other a 0. On the other hand, if they add up to 2 or 0 and there are still votes, the individual must have either voted for both options or none of them. In this case, the individual will automatically be requested to vote again. Notably, throughout this whole procedure, the verifier did not extrapolate any information on who the entity voted for, rather if their vote is valid – true. This ZKP has the potential to placate significant concerns faced by voters in regards to their privacy.
Privacy Tokens and Private Transactions
In addition to offering novel layers of security and privacy to voting, ZKPs are used directly in certain blockchains to establish absolute concealment of transactions. Through the use of zkSNARKs, entities can send and receive tokens via a blockchain without their transaction details, including their address, amount and relevant tokens, being publicly available information. Nonetheless, this offering is congruent with one of the fundamental benefits provided by blockchains – transparency. The transaction appears on the public blockchain, yet all of the information is encrypted via the zkSNARK. Blockchains like Zcash and Monero offer this functionality, seeing them respectively average 45k and 16k shielded transactions per day.
Likewise, Aztec is another crucial part of the ZK-privacy industry; however, as opposed to being its own blockchain, Aztec is a layer 2 network that both scales Ethereum and brings privacy to its mainnet. Similarly to Zcash and Monero, this platform utilises zkSNARKs to compress transactions that took place on its network, yet does not include transaction data in the rollups that are posted to Ethereum. Nevertheless, Aztec guarantees that all state changes detailed in the ZKP it generates can be verified without sacrificing privacy. Furthermore, the layer 2 enables users to leverage its technology to interact with DeFi protocols on Ethereum.
Furthermore, protocols built on blockchains make use of ZK cryptography. Tornado Cash is one such platform; the popular cryptocurrency mixer allows users to increase their anonymity by “mixing” tokens together, making it arduous to track its past owners. Despite the potential for this platform to be misused, it enables individuals and entities to freely and confidentially use the blockchain without fear of being tracked. The benefits of protocols like Tornado Cash herald are only possible by ZKPs. Sharing data and information about the transactions would negate the privacy crypto mixers offer, hence, to obfuscate this information whilst ensuring its truth, Tornado Cash relies on discoveries in the ZK industry.
Privacy-Preserving Data Storage
With millions of individuals and companies making use of data storage services, the risk of their personal information and files being shared is high. Despite the growth of decentralised storage options, such as Filecoin, which stores just under 305 PIBs of data, this threat remains. However, as more of these blockchains look to integrate deeper layers of privacy into their storage systems, they are turning to ZKPs. Differing from ZKPs that conceal transaction details or allow mixers to function, the proofs that these platforms are using encryption techniques to ensure that network participants are unaware of the data uploaded on the chain, irrespective of the fact that they are storing it.
Although ZK encryption techniques have many prospects in the decentralised data storage platforms, its benefits extend to the web2 world. To offer increased security and privacy for its clients, cloud services are adopting ZKPs when encrypting data on the client side. Accordingly, these platforms, including popular cloud services like Sync and pCloud, offer its clients assurances that neither the storage providers nor backup providers will obtain access to their data.
Future Applications of Zero-Knowledge Proofs
Digital Verifiable Identities
Evident from the above use cases, ZKPs have many applications with respect to privacy and effectively encrypting confidential information. Despite the strides being made to protect user data through ZKPs, this cryptography has not yet adequately been integrated into digital identities. As web3 edges closer to obtaining mainstream recognition and more entities are onboarded, safely securing identities becomes an increasingly important issue. Blockchain will likely become the infrastructure which stores individuals’ digital identities that they utilise throughout their online interactions.
Digital verifiable identities (DVIs) leverage non-transferable NFTs that can be burnt by the issuer to create an individual’s identity. These NFTs can be used for a multitude of purposes; from university degrees, existing bank loans, on-chain resumes and more, these life experiences will form one’s blockchain-based identity. As well as DVIs, discussions around digital IDs have grown in popularity subsequent to a recently published paper, “Decentralized Society: Finding Web3’s Soul”, which accentuates the burgeoning need for this technology in the form of SoulBound Tokens (SBTs).
Yet, although the identity related data tied to these DVIs will be revealed upon the owner’s permission, this process of decrypting such information heralds the possibility of exploits, potentially leading to identity theft. Here is where ZKPs have an important role to play. Through this cryptography, entities will be able to establish the validity of personal information through DVIs or SBTs without revealing any details about themselves publicly. In this way, individuals will be able to grow their digital identity without the fear of this data being stolen or obtained by malicious third parties.
Combating MEV Through Zero-Knowledge Ethereum Mempool
Beyond the future applications of ZKPs with respect to privacy, the technology can be used to protect transactors from the “invisible tax” of Maximal Extractable Value (MEV). As explained in our article on MEV, miners and validators have the capacity to strategically determine the order of transactions in a block, inserting their own transactions and preventing others, to ensure they generate the most profit. However, capturing MEV functions similarly to free markets, in the sense that making money in a zero-sum game; one party financially benefits at the expense of another party’s fiscal detriment.
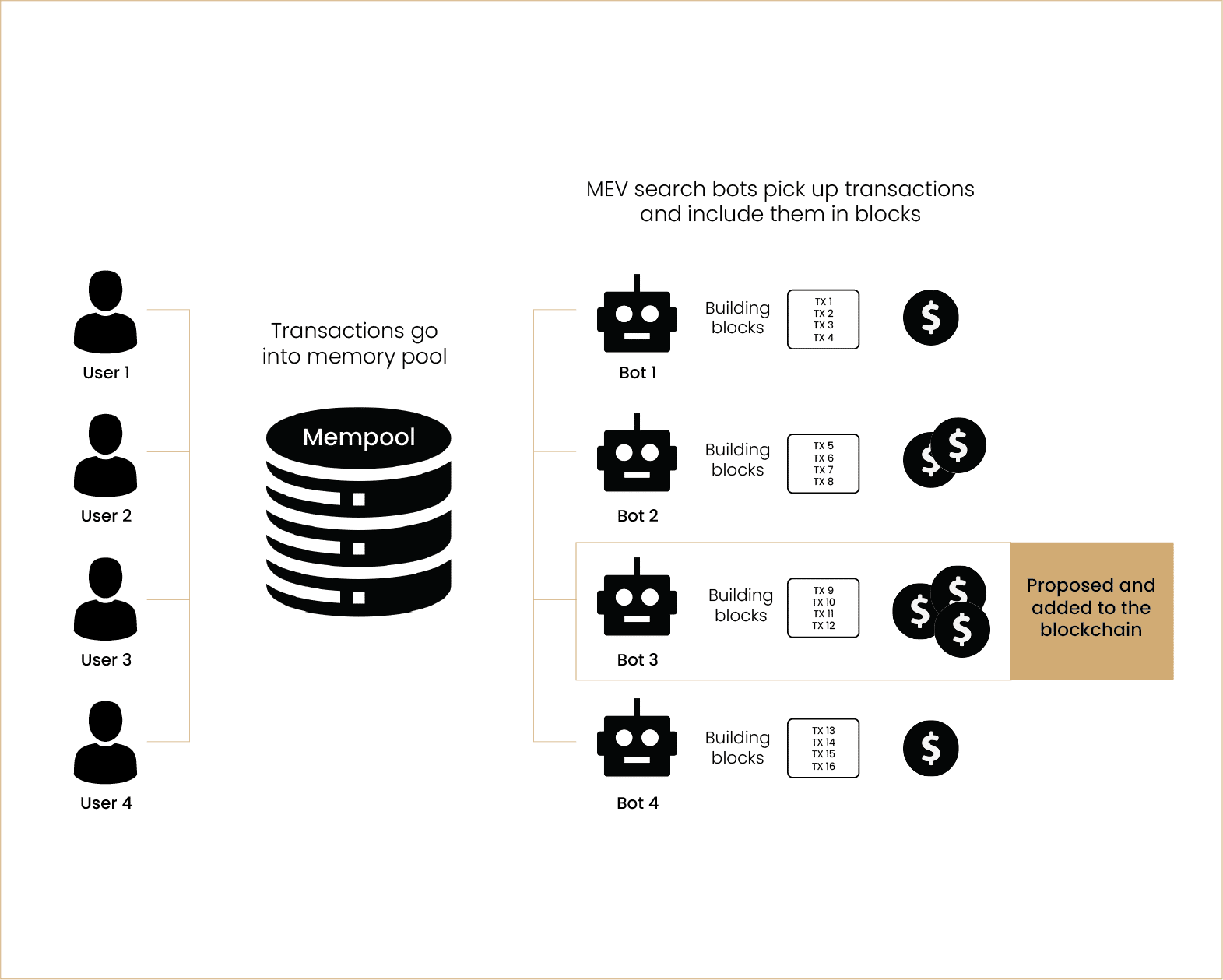
Within the confines of blockchain technology, validators organise transactions to profiteer off unknowing users given they can see their transactions entering the mempool. Solutions are frequently proposed to alter the mempool so as to mitigate the negative externalities emerging from MEV; these include single-slot finality, a committee-based finality model. As well as altering finality efficiency, using ZKPs to encrypt the mempool could prove to be a comprehensive panacea to MEV. Notably, the Ethereum whitepaper initially established gas to be a way for users to bribe block builders. Hence, gas was the primary means by which block builders could increase profit per block. ZKPs can be utilised to hide transaction information that extend beyond the bribe (gas) being offered by a user; one could verify that a certain entity is offering more than another with no other data being available.
Negating MEV through a ZK mempool could bring numerous and meaningful benefits to Ethereum and other blockchains. Toxic, malicious MEV could be abolished as bad actors no longer have the sufficient information to order transactions at the detriment of DeFi users. In addition, the use of ZKPs could increase blockchains’ level of censorship resistance as validators cannot automatically leave out transactions from certain wallet addresses. The space is already seeing issues relating to this form of censorship with Flashbots being OFAC-compliant, resulting in more than 70% of blocks since the merge barring transactions sent by wallets banned by the OFAC.
ZK Auctions
Both inside and outside the web3 world, building effective auction mechanisms that accurately and objectively value items is challenging. Currently, there are four primary auction types widely used, all are plagued with various shortcomings. English auctions, also known as ascending-price auctions, start at a reserve price and incrementally increase until only a single bidder remains. Contrastingly, Dutch auctions decrease in value according to a pre-established schedule; the first bidder is the winner as this individual will only bid at the value they believe the item being sold is worth. Furthermore, First-Price Sealed-Bid auctions sees all relevant parties submit a sealed bid before the highest bidder is announced as the winner when this individual or entity pays the price they offered. Finally, Vickrey auctions, also referred to as Sealed-Bid Second-Price auctions, function similarly to first price sealed-bid auctions, however the highest bidder pays the price offered by the second-highest bidder. Overall, sealed-bid auctions have thus far proven difficult to implement on-chain, hence have not seen much adoption.
ZKPs can revolutionise how sealed-bid auctions are used in the web3 industry. A proof can be written that establishes that the bidder has locked the relevant amount into the offer and that this value is higher than any other value. No other information about the holistic wealth of the bidder or the monetary value of other bids will be revealed. As such, items, both on-chain and in the real world, can be valued fairly based on individuals’ viewpoints rather than being influenced by pride, emotions and other similar factors. Moreover, the integration of ZKPs into these on-chain auctions limits the efficacy of intrinsic shortcomings of existing models.
Conclusion
Despite the nascency of ZK technology in the crypto industry, its various and beneficial applications are growing increasingly clear. From scaling blockchains like Ethereum, upholding privacy in the fields of data storage, identities and transactions as well as remedying the plague of MEV, ZKPs are gradually becoming more congruent with the general cryptocurrency roadmap. With more cognisance for the advantages of these proofs on behalf of builders, developers and cryptographers in the space, ZKPs are poised to see meaningful adoption and be applied to many more areas.
About Zerocap
Zerocap provides digital asset investment and digital asset custodial services to forward-thinking investors and institutions globally. For frictionless access to digital assets with industry-leading security, contact our team at hello@zerocap.com or visit our website www.zerocap.com
DISCLAIMER
Zerocap Pty Ltd carries out regulated and unregulated activities.
Spot crypto-asset services and products offered by Zerocap are not regulated by ASIC. Zerocap Pty Ltd is registered with AUSTRAC as a DCE (digital currency exchange) service provider (DCE100635539-001).
Regulated services and products include structured products (derivatives) and funds (managed investment schemes) are available to Wholesale Clients only as per Sections 761GA and 708(10) of the Corporations Act 2001 (Cth) (Sophisticated/Wholesale Client). To serve these products, Zerocap Pty Ltd is a Corporate Authorised Representative (CAR: 001289130) of AFSL 340799
All material in this website is intended for illustrative purposes and general information only. It does not constitute financial advice nor does it take into account your investment objectives, financial situation or particular needs. You should consider the information in light of your objectives, financial situation and needs before making any decision about whether to acquire or dispose of any digital asset. Investments in digital assets can be risky and you may lose your investment. Past performance is no indication of future performance.
FAQs
What are Zero-Knowledge Proofs (ZKPs) and how do they work?
Zero-Knowledge Proofs (ZKPs) are a mathematical concept that allows one party to prove to another that a statement is true, without revealing any information about the statement itself. This cryptographic breakthrough has significant applications in the blockchain space, particularly in terms of data compression and security.
What are the origins of Zero-Knowledge Proofs?
The concept of ZKPs was first introduced in a 1985 paper by Shafi Goldwasser, Silvio Micali, and Charles Rackoff. Their work laid the groundwork for simple interactive proofs in nondeterministic polynomial time, providing a means to prove certain statements as true without revealing information about those statements or the data used to construct them.
What are the dominant types of Zero-Knowledge Proofs?
The two dominant types of ZKPs are zk-SNARKs (Zero-Knowledge Succinct Non-Interactive Argument of Knowledge) and zk-STARKs (Zero-Knowledge Scalable Transparent Argument of Knowledge). zk-SNARKs generate proofs to demonstrate knowledge using secret keys without interacting with the verifier. zk-STARKs, on the other hand, eliminate the need for a trusted setup of cryptographic keys and primarily rely on hash functions.
What are the current and potential future applications of Zero-Knowledge Proofs?
Currently, ZKPs are primarily used for scaling Ethereum and assisting in achieving its rollup-centric roadmap. They are also used in voting systems, privacy tokens and private transactions, and privacy-preserving data storage. Future applications could include digital verifiable identities, combating Maximal Extractable Value (MEV) through Zero-Knowledge Ethereum Mempool, and Zero-Knowledge auctions.
How do Zero-Knowledge Proofs contribute to privacy and security in blockchain technology?
ZKPs contribute to privacy and security by allowing for the verification of transactions and data without revealing the underlying information. This ability to establish truth without revealing how that truth was reached or the contents of what underpins the truth has clear use cases in conveying data without the fear that the veracity of the data will be questioned or undermined. This is particularly useful in the context of trustless blockchains.
Like this article? Share
Latest Insights
Weekly Crypto Market Wrap: 21st July 2025
Zerocap is a market-leading digital asset firm, providing trading, liquidity and custody to forward-thinking institutions and investors globally. To learn more, contact the team at
Weekly Crypto Market Wrap: 14th July 2025
Zerocap is a market-leading digital asset firm, providing trading, liquidity and custody to forward-thinking institutions and investors globally. To learn more, contact the team at
Zerocap selects Pier Two to offer institutional staking yields
Institutional clients gain secure, non-custodial access to native crypto yields with top-tier infrastructure Leading digital asset firm Zerocap has selected global institutional staking provider Pier
Receive Our Insights
Subscribe to receive our publications in newsletter format — the best way to stay informed about crypto asset market trends and topics.



 Share
Share  Tweet
Tweet  Post
Post 